With every cyber attack, it becomes increasingly clear that no one is safe from data breaches or cyber extortion. Whether you’re an employer that stores proprietary data or an individual with financial and personal information at risk, hackers won’t rest until they have what’s yours. And their tactics continue to evolve.
Cyber criminals have a variety of tools and techniques at their disposal, including malware, ransomware and disrupted denial-of-service attacks. One of the most common and difficult-to-spot strategies hackers use is phishing scams, which require minimal technical know-how and can be deployed from anywhere in the world via a simple email.
In broad terms, phishing is a method cyber criminals use to gather personal information. In these scams, phishers send an email or direct users to fraudulent websites, asking victims to provide sensitive information. These emails and websites are designed to look legitimate and trick individuals into providing credit card numbers, account numbers, passwords, usernames or other sensitive information.
76% of organizations reported being a victim of a phishing attack in 2017.
With every opened email, users risk becoming the victim of monetary loss, credit card fraud and identity theft. What’s more, successful phishing attacks oftentimes go unnoticed, which increases the risk of large and continued losses, particularly for businesses.
Even in the face of highly funded cyber security measures, phishing scams can be financially devastating. In 2017, tech giants Facebook and Google were phished for over $100 million each, proving that protection from online scammers doesn’t come easy—even for Fortune 500 companies.
Phishing is becoming more sophisticated by the day, and it’s more important than ever to understand the different types of attacks, how to identify them and preventive measures you can implement to keep yourself safe.
Phishing vs. Spear Phishing
Often, the terms phishing and spear phishing are used interchangeably. However, there is a key distinction between these two types of attacks, and it’s important to have some basic background knowledge.
According to a report from the Ponemon Institute, human error accounted for nearly 30% of worldwide data breaches.
Phishing attacks
Phishing is a general term that refers to any cyber attack where a hacker disguises themselves as a trusted source in order to acquire sensitive information. Typically, under traditional phishing attacks, hackers send fraudulent, malicious emails to as many people as possible. It’s not unusual for phishing attacks to target thousands of individuals at once in the hopes of netting just a few victims.
Phishing attacks take a quantity over quality approach. Despite the randomness of the attacks, phishers can gain highly sought information on their victims through mass, easy-to-reproduce emails. The goal of these emails is to compromise data or a larger network through the greatest cyber security vulnerability of all—users themselves. Effectively, instead of going through the hassle of breaking strong, digital defenses, hackers use phishing attacks to trick someone into giving them access to a network or data.
To fool the victims, attackers customize phishing emails to make them appear legitimate, sometimes using logos or dummy email accounts to improve the effectiveness of the attack. Usually, phishers will pretend to be a trusted source, like a hospital, bank or employer. The phishing message will likely include alarming or suggestive language to fool victims into:

If a victim does any of the above, the hacker can infect their computer and steal sensitive information, often without having to use a single line of code. With phishing attacks, even the most top-of-the-line firewall can’t stop an individual from clicking on a malware-loaded email. And, once a single computer gets infected, the malware can spread throughout an entire network.
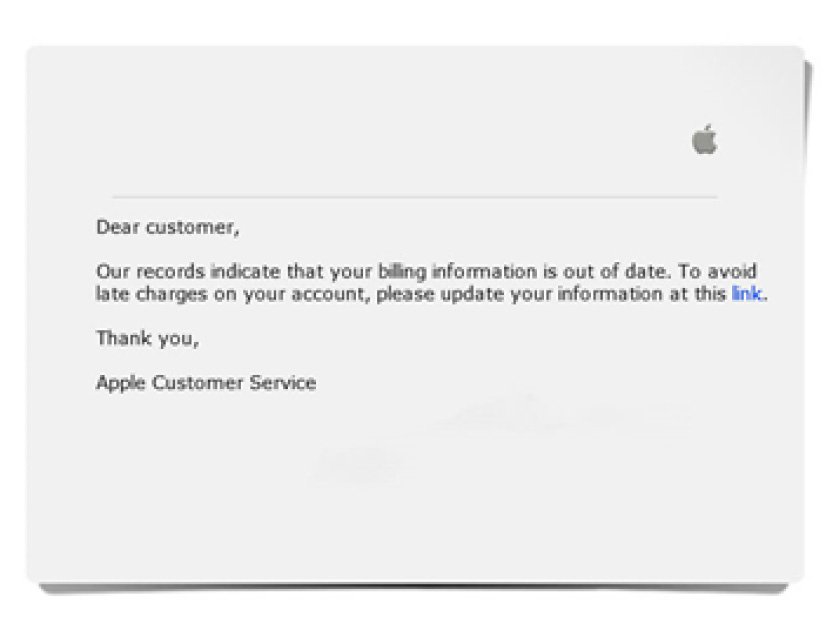
Here’s an example of a phishing email, in which the phisher is impersonating a popular company (Apple) in order to trick you into clicking a link. This link could redirect you to a fraudulent website to either steal your personal information or install malicious software on your device.
Spear Phishing
While phishing attacks are effective, they are designed to be broad and affect as many individuals as possible. As a result, they are generally written vaguely and are easy to spot. Spear-phishing attacks are much more convincing, targeted and sophisticated.
With spear phishing, cyber criminals narrow down the scope of their attack to a smaller group, sometimes just a handful of individuals. By doing this, hackers can do research and make the phishing email much more convincing based on a victim’s profile or online activity. Malicious hackers can find most of the information needed to carry out a spear-phishing attack right on the internet, particularly on company websites and social networking sites. It’s not uncommon for phishers to use a target’s personal information (e.g., name or address) or the personal information of their friends, family and colleagues as leverage in an email.
Because spear-phishing attacks are highly customized, they are far more likely to succeed than traditional phishing attacks. What’s more, spear-phishing attacks often have specific goals. For instance, a phisher may target certain individuals based on whom they work for, the type of information they have access to or their financial status. Spear-phishing attacks may focus on a particular company, organization, group or government agency based on the potential ROI.
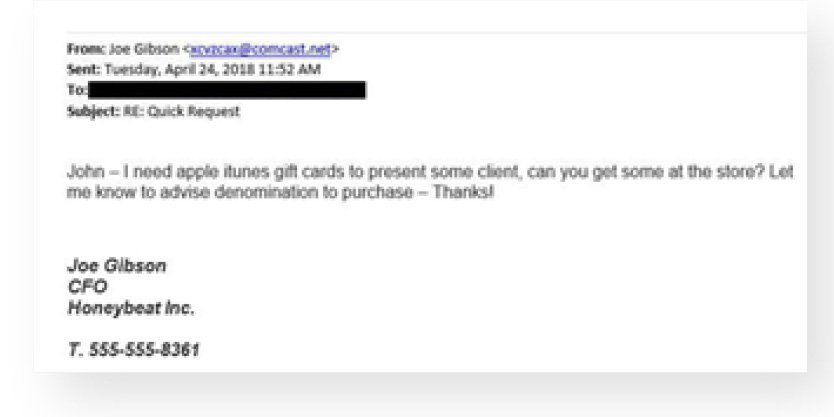
Here’s a sample of a spear-phishing email. In this example, the phisher is impersonating an executive of a company and asking an employee to complete an urgent task for them. Here, the phisher is hoping to trick the user into replying to the email, which could help the cyber criminal steal or gather sensitive information.
What’s at Risk?
Of all the various types of cyber crime, phishing attacks are some of the most dangerous. This is because phishing messages can easily bypass standard anti-virus software and pass through spam filters. What’s more, scammers don’t need to infect your computer with a virus to obtain your information. Instead, criminals rely on psychology and misdirection.
Simply by clicking links, replying to an email or completing forms found in fraudulent emails, you give hackers all the information they need.
Following a phishing attack, employers and individuals could lose any of the following information:
- Login credentials
- Banking credentials
- Credit and debit card information
- Addresses and other personal information
- Trade secrets
- Confidential documents
- Medical information
For businesses, the risks of phishing are magnified because, by infecting a single user, hackers can launch even more penetrating attacks on an organization’s network, stealing credentials, disrupting critical processes, or encrypting data and making it impossible to access.
Get Informed, Stay Protected
Cyber attacks, including phishing schemes, aren’t going away. In fact, they’re becoming more sophisticated. It’s no longer enough to simply install anti-virus and anti-malware software. To truly protect yourself, it’s crucial to stay informed on the most recent cyber attacks and up-to-date protection strategies.
In addition to providing risk management tips for both employers and individuals, CoverLink Insurance can help keep you informed on the biggest happenings in cyber security and cyber insurance. Contact us today to learn more ways to stay cyber safe.
