Prior to the global ransomware cyber attack known as WannaCry, cybersecurity was an issue widely ignored by the general public, government and businesses.
However, in the wake of the cyber attack, many organizations are revisiting their position on cyber security.
Why?
Because this attack proves that no business or organization, regardless of size, is immune.
What is WannaCry?
The WannaCry ransomware that some are referring to as the largest global cyber attack in history, quickly spread to universities, hospitals and businesses across 150 countries in just a few short days.
It left many trying to determine if they should pay the ransom to regain access to their own files, or rely on their backups to avoid giving in to the attackers. Some people are saying that the same attackers are behind the disasterous Sony Data Breach a few years ago.
This form of ransomware locked users out of their computers by exploiting a vulnerability in outdated versions of Microsoft Windows. It then demanded money from users who wanted to regain control of their data.
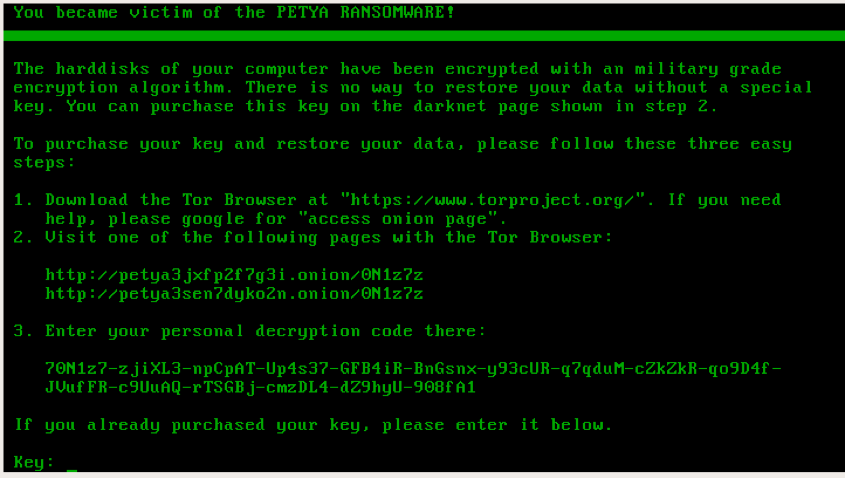
The ransomware initially requested around $300, and if no payment was made, threatened to double the amount after three days, and delete files within seven days.
Once it infected one computer, it could spread to every computer in that network within seconds.
After the initial discovery of the WannaCry ransomware, Microsoft issued a warning to the U.S. government concerning its data-storing practices.
Microsoft claimed that the tool used in the WannaCry cyber attack was developed by the U.S. National Security Agency and was stolen by hackers. Microsoft released a Windows security update in March to tackle the problem exposed by the latest attack. However, many corporations hadn’t run the update yet because Windows updates can have a serious impact up their legacy software programs.
In addition, many consumers were at risk because, while Microsoft requires Windows 10 customers to automatically update their computers, many people with older PCs have disabled automatic updates.
Unfortunately, we haven’t even seen the widespread lasting effects of this cyber attack, but we do know it underlines the growing problem of ransomware.
Ransomware is a growing trend

“Never before in the history of humankind have people across the world been subjected to extortion on a massive scale as they are today.” –The Evolution of Ransomware, Symantec Report.
Ransomware has been a growing trend for the past several years, and the WannaCry attack is just a culmination, a grand reveal, to the wider world of just how big of a threat it is.
Ransomware is a sophisticated piece of malicious software, or malware, that blocks the victim’s access to his or her files. It infects a desktop or laptop computer, sometimes locking up the machine, but more often encrypting data and files, rendering them unusable. Then an ominous message from the attacker pops up, demanding a ransom be paid in order to unlock the computer or decrypt the data. How the cyber criminals transmit their malicious software is becoming increasingly sophisticated, as they reach end-users computers through programs like Adobe Flash Player, Microsoft Internet Explorer and Microsoft Silverlight.
Ransomware creators are constantly embedding advertising, shopping and other highly trafficked online networks with their software, which seeks out browser vulnerabilities and infects computers when the end-users click on activating links.
In addition, they will use spam emails that contain an attachment including ransomware. The email is often disguised to look like it is from a bank or delivery service, or even the IRS.
Then comes an urgent ransom note, intended to scare the victim into paying-up, or else. And the victim is left with a decision to either pay the extortionist, or lose valuable files forever.
How can individuals and small businesses protect their data?

Unfortunately, in today’s technology driven world, there is no guarantee in preventing a cyber attack. Every organization is vulnerable, as you can see with the high profile companies who were victims of the WannaCry attack (i.e. FedEx).
However, there are some actions that an organization should take to protect its data, including:
- Make sure you have backups. Your backups should be on a separate source or a cloud storage service, as any servers, hard drives or other backup sources connected to a network will probably be infected, too. At least one backup should also be stored in a different physical location.
- Keep browsers, plug-ins and operating systems up-to-date. When you see the update requests, make sure you do as they say. You can also purchase an additional layer of protection with anti-virus software programs.
- Urge everyone to be extremely cautious with spam. Never download unknown files or click on unknown links.
Ransomware implications for small and medium-size businesses
Conceivably, every business and consumer using the internet is a potential target for ransomware perpetrators, though small and medium-size businesses have become particularly easy marks.
Large companies typically have IT departments and robust cybersecurity programs, while small and medium-sized businesses lack the resources and defense programs to protect themselves.
If a small business suddenly has all of its data encrypted and the only way to recover their customer information, contracts, legal documents and more is to pay $1,000, they will likely pay the ransom.
It’s worth the $1,000, especially considering that the National Security Alliance has estimated that 60% of small businesses hit by a cyber attack go out of business within six months.
However, what happens when a small business’s data is being held as ransom for thousands of dollars? For example, in February 2016, Hollywood Presbyterian Medical Center was locked out of its hospital’s computer systems and held for ransom of 40 bitcoin (equivalent of $17,000).
Systems affected included computers that handle lab test results and pharmaceutical orders, even the emergency room staff wrote all documentation by hand while offline. After a week of negotiations, internally and externally, the ransom was paid and the files were restored.
A small business may not be able to afford to pay a large ransom to restore files. If the files are not restored, a small business may be faced with purchasing all new computers, programs and more.
Or, what about the business interruption or downtime that a business suffers while the files are locked? Even if a business pays the ransom and the files are restored, do you trust that those files haven’t been tampered with?
In these cases a cyber liability insurance policy would be vital to the survival of the business.
Cyber Liability Insurance
Cyber Liability Insurance typically reimburses the costs you incur in the event of a data or information breach. There are many variations among policies and premium costs for cyber security insurance in Ohio, but two distinct risk categories can be determined and this is a good place to start: first-party and third-party liability.
First-party vs. third-party Liability
First-party liability is where your or your business’ private information is breached. This could look like a virus or malware damaging internal IT systems or tax records being exposed.
Third-party liability is when the private information of your clients is breached such as a hack into the Netflix user database where account information is compromised.
Both of these categories of liability are relevant to companies of all sizes:
According to Debbie Foister, Manager, Forensic Services: “A recent study by the U.S. Secret Service indicates that more than 72% of data breaches occur in small to medium-size companies with an estimated average cost of a data breach being placed at more than five million dollars. First-party cyber liabilities can threaten a company’s liquid assets and competitiveness. Third-party cyber liabilities can be more devastating because it often ruins brand image and reputation, encourages sizable dollar lawsuits and initiates statutory fines”
The risks are high and this is why data breach insurance is so important for all businesses today. It’s now often said that it’s not a matter of if you will be breached, but when? And further, when will the breached data be used against you.
Regardless of the type of business, one thing is certain, if you’re a business in operation today, you face multiple cyber liability risks.
Which means, you need to thoroughly understand your risk of a loss, how you would respond if a loss did occur, and whether Cyber & Data Breach Liability coverage makes sense for you.
Types of cyber coverage to consider when fighting against ransomware
- Cyber Threats or Extortion: reimbursement for payment resulting from a threat to prevent access to your computer system, introduce a virus to your system, reveal your confidential information, or damage your brand or reputation by posting false comments on social media sites.
- System Damage: costs you incur to retrieve, restore or replace any of your computer programs that are lost or damaged.
- Business Interruption: replacement of your lost income resulting from a computer system outage because of a cyber attack.
- Regulatory Actions or Investigations: coverage for costs, expenses, fines and penalties as a result of a regulatory investigation arising out of an actual or suspected breach.
The level of coverage your business needs is based on your individual operations, and can vary depending on your range of exposure. It’s important to work with an Insurance Advisor that can identify your areas of risk, and customize a policy to fit your unique situation.
Incident response plan
According to the NTT Security’s Global Threat Intelligence Report, which analyzed over 6.2 billion cyber attacks in 2017 alone, only 32% of organizations have an incident response plan.
 Further, a study conducted by the Ponemon Institute found that 78% of businesses who do have a response plan in place, do not regularly update their plan to account for changing threats, or changes within their organization.
Further, a study conducted by the Ponemon Institute found that 78% of businesses who do have a response plan in place, do not regularly update their plan to account for changing threats, or changes within their organization.
These statistics are alarming, especially considering that the National Security Alliance has estimated that 60% of small businesses hit by a cyber attack, go out of business within six months.
Not only should you be taking steps to keep your data safe to prevent an attack and arming yourself with an appropriate cyber liability insurance policy, but you should have an incident response plan in place to help your business recover.
Creating, implementing and improving your plan
Because a typical data breach involves a long list of moving parts that often need addressed simultaneously, it’s important to establish a response plan that takes into account a variety of scenarios and responsibilities that could come into play.
There’s no one-size-fits-all data breach response plan. That being said, we have outlined 10 suggested steps that will help you create, implement and improve upon a data breach response plan for your business.
- Research any legal issues: Research any federal or state laws that may apply to your business and keep this information up-to-date.
- Research any prominent or emerging technologies: Consider any technologies that could impact the scope of a breach, or impact how you could protect yourself from damage.
- Assemble an internal response team: Identify your internal response team in advance by establishing roles and responsibilities.
- Assemble an external response team: Depending on the size of the data breach and the size of your organization, you may need to rely on an external response team. Determine your strategic partners, establish a relationship with them, and make a list of those partners ahead of time.
- Outline a strategy for identifying and containing the breach: Acting quickly and strategically following a data breach is extremely important – identify who will be responsible and the steps they should follow.
- Outline a notification strategy: Ensure that notification to any injured parties is provided in a prompt fashion by outlining your strategy ahead of time.
- Develop an internal communication strategy: Outline a process for internal reporting to ensure that everyone from the response team is up-to-date and on track during a breach.
- Develop an external communication strategy: Outline the strategy for communicating with the media and responding to external inquiries.
- Conduct preparedness training: Practice and test your preparedness plan and perform regular reviews.
- Prepare for the worst: Prepare for the worst so you are able to respond with your best.
We can help you recover from a data breach
Businesses are operating in an environment where it’s not a matter of IF a data breach will occur, it’s only a matter of when.
We need to take reasonable measures to reduce the likelihood of a breach, but we also need to be realistic and understand that inevitably, we’ll all deal with a data breach at some point.
The two most important questions you need to answer as a business owner are:
- Will I know how to respond when a breach occurs?
- Will my business survive the devastating consequences of a data breach?
The planning you do today, the strategic partnerships you put in place, and the adequacy of your Cyber & Data Breach Insurance coverage are all critical components to confidently answering the question of ‘will my business survive after a data breach’ with a resounding ‘ABSOLUTELY.’
We understand the negative effects a data breach can have on your organization, we’ve seen first-hand how it impacts clients. We also know which insurance companies provide the broadest insurance coverage to help you recover after a breach occurs.
But we don’t stop there.
The best place to begin is with your own internal operations, the security measures you have in place, and the controls implemented to avert a data breach.
In addition providing the Cyber & Data Breach Liability coverage, we can also provide you several services that will help position your business for the best insurance premiums offered by the nation’s strongest insurance carriers. Specifically, we can:
- Provide you with data security resources designed to help keep your data, and your network, safe
- Perform a data breach risk assessment of your business to help identify areas of weakness, and offer solutions to mitigate the exposures
- Help you develop and implement an Incident Response Plan
To learn more about the ways we can help simply Request a Proposal and we’ll get to work right away.
