In a distributed denial-of-service (DDoS) cyberattack, a cybercriminal attempts to interrupt an online service by flooding it with fake traffic. During a DDoS attack, a network of infected computers overwhelms a victim’s IP address with requests. The goal is to exceed the capacity limits of their websites, servers and networks, resulting in a halt of services. And DDos attacks are on the rise.
DDoS attacks are classified as network and website disruption losses in Advisen’s database. From 2011 to 2021, network and website disruption losses increased 550%, according to Advisen data, a concerning trend as these events can also be quite costly for the victim. In fact, one research group found the average cost of a DDoS attack is $218,000.
Read on to better understand what’s driving the increased frequency of DDoS attacks, the industries most impacted (according to Advisen data) and tips for avoiding becoming the next victim.
DDoS Attacks Explained
DDoS attacks occur when a hacker infects devices with malware and creates a network of remotely controlled computers called a botnet. Botnets can consist of millions of computers that can be located anywhere and belong to anyone. The hacker then instructs the botnet to flood its victim with more connection requests than they can handle.
DDoS cyberattacks originate from various sources, which may include disgruntled employees, competitors or nation-state actors. The attackers may seek to enact revenge, cause chaos or gain a competitive advantage. DDoS attacks can also involve extortion, in which perpetrators install ransomware on servers and demand payment to reverse the damage.
The Increasing Frequency of DDoS Attacks
DDoS attacks are increasing at an alarming rate. Some factors contributing to this rise include:
- Internet of Things (IoT) devices—The number of IoT devices is rising rapidly. In 2021, the number of active endpoints globally rose 8% to 12.2 billion. By 2030, this number is expected to surpass 25.4 billion. But as the number of connected devices grows, so does the number of available devices for hackers to turn into botnets; IoT devices are especially vulnerable because they rarely have built-in firmware or security controls. The increasing number of IoT devices will allow hackers to create broader networks of computers, strengthening the size of the attacks they can level against their victims.
- Application programming interfaces (APIs)—APIs are small pieces of code that allow systems to share data publicly. Public APIs may have a number of vulnerabilities, including weak authentication checks, lack of robust encryption and flawed business logic. In a DDoS attack, APIs can be attacked on both ends of the service. This means your API may be attacked from the server and the API server simultaneously, significantly increasing the strength of an attack.
- Cyberwarfare—War and international tensions can lead to an increase in hacktivist-driven cyberattacks. The term “hacktivist” is used to describe cybercriminals who are ethically, politically or socially motivated. Hacktivists may use DDoS attacks to make a statement or retaliate against people, governments or organizations they don’t agree with, among other reasons.
- Ransomware/extortion—Cybercriminals are increasingly partnering DDoS attacks with ransomware/extortion demands. This way, DDoS attacks can increase the pressure on victim companies and bring them back to the negotiation table following a refusal to pay a ransom.
Losses in Advisen’s database give a glimpse into the increasing frequency of DDoS attacks, the industries most affected by this type of cyberthreat and the consequences of such attacks.
Advisen Data – Network and Website Disruption Losses by Year
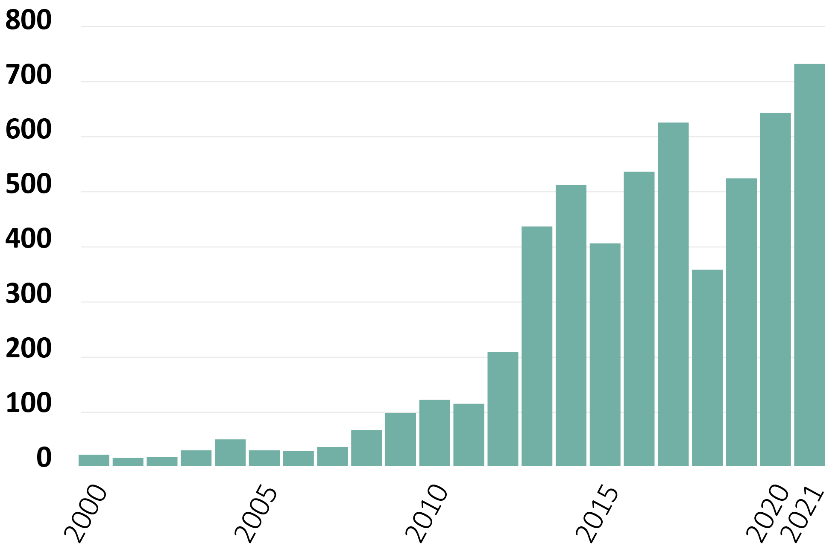
Network and website disruption losses reached an all-time high in 2021. The record-breaking year comes after a decade of significant increase.
Network and Website Disruption Losses by Industry
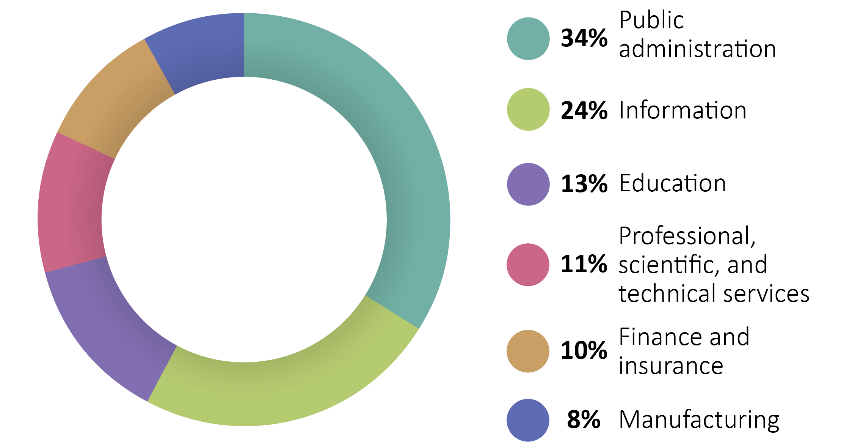
Network and website disruption losses pose a threat to organizations across all industries. However, some industries are more prone to this type of cyber incident than others.
According to Advisen data, public administration sees roughly one-third (34%) of all network and website disruption losses. One reason may be that public administration includes state and local governments, which are a frequent target of hacktivists. Additionally, malicious actors may also target public administration to disrupt communication and limit information to weaken governments.
The information sector sees the second most frequent amount of network and website disruption losses at 24%. This sector, which comprises broadcasting, telecommunications and publishing companies, may be a preferred target since they are often well known and highly visible, increasing the chance the press will cover the attack.
Impact of Network and Website Disruption
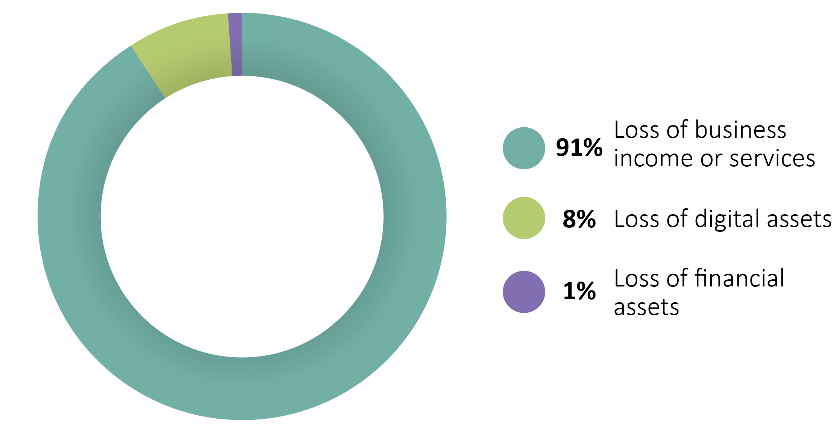
Losses
Loss of business income or services is the most common consequence of a network and website disruption loss. However, Advisen data shows that a loss of digital assets is also present in 8% of network and website disruption losses. Loss of digital assets refers to the corruption or destruction of corporate data or software as the result of a network failure. Additionally, a loss of financial assets (i.e., bank deposits, bonds, cash or contracts) resulted from 1% of network and website disruption losses.
Fortunately, there are a number of measures organizations can implement to identify and block DDoS attacks.
Identifying DDoS Attacks
The symptoms of a DDoS attack may resemble commonplace technological issues. Therefore, it’s important for organizations to be aware of the following warning signs:
- Slower loading times
- Inability to access certain websites
- Trouble accessing the internet
- An excessive amount of spam emails
To protect vital network functions from DDoS attacks, it’s important for all organizations to have prevention plans in place.
Preventing DDoS Attacks
Organizations should consider the following steps to avoid and mitigate DDoS attacks:
- Use a virtual private network (VPN). VPNs mask and encrypt IP addresses and other identifiable network elements.
- Install antivirus software. Antivirus software can identify and block the types of malware used by DDoS hackers.
- Enroll in a DDoS protection program. DDoS protection services are designed to identify abnormal traffic and direct it away from company networks.
- Evaluate security practices. Keep good security practices. This includes limiting the number of people with access to important information and managing unwanted traffic.
- Create a disaster recovery plan. Plan ahead to create a communication, mitigation and recovery plan in case of a cyberattack.
- Secure sufficient insurance coverage. It’s critical to purchase adequate insurance to help protect against losses that may arise from DDoS incidents. It’s best to consult a trusted insurance professional to discuss specific coverage needs.
Conclusion
DDoS attacks are a rising concern for organizations. By implementing proper prevention strategies and having response plans in place, businesses can protect themselves against this cyberthreat. If you’d like additional information and resources, we’re here to help you analyze your needs and make the right coverage decisions to protect your operations from unnecessary risk. You can download a free copy of our eBook, or if you’re ready to make Cyber Liability Insurance a part of your insurance portfolio, Request a Proposal or download and get started on our Cyber & Data Breach Insurance Application and we’ll get to work for you.
